CDT-Internet
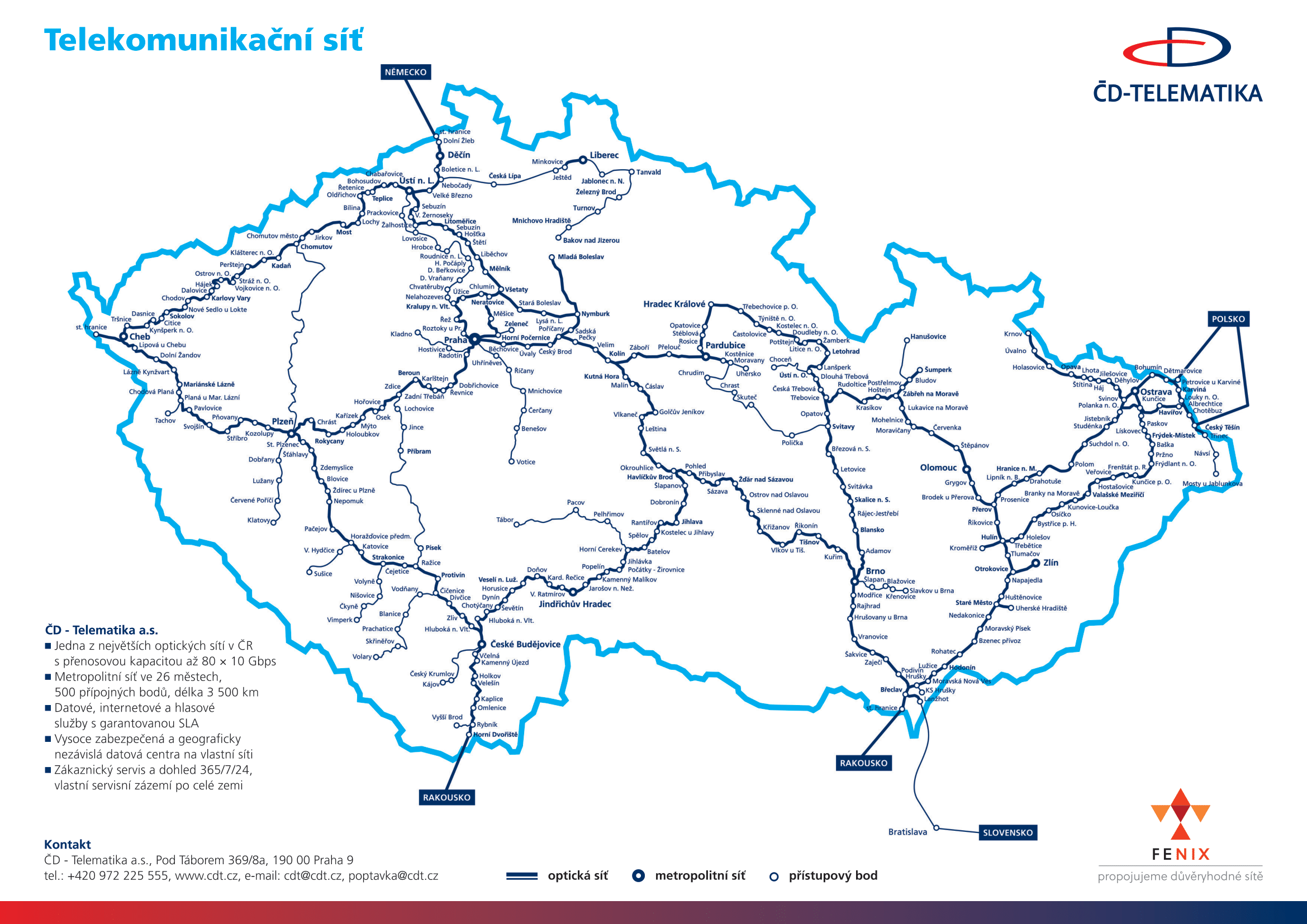
The ČDT-Internet service provides Internet access via the ČD - Telematika network. The product is particularly designed for customers who need a high-quality and reliable Internet connection. ČDT-Internet offers an access circuit and Internet connectivity.
FENIX - Connecting trusted networks.
Service parameters
- Internet access
- Required number of IP addresses
- Fixed access line
- Service availability guaranteed by SLA (Service Level Agreement)
- Technical support and troubleshooting assistance 24 hours a day
- Continuous network monitoring
- Range of transfer rate: between 2 Mb/s and 20 Gb/s
- Interface provided: G.703/704, G.957, Ethernet, FE, GbE, 10GbE, 100GbE
Main benefits
- Guaranteed availability of NIX.CZ national node and access to peer nodes abroad
- Reserved transfer capacity without aggregation
- Reliable transmission technology
- Quick upgrade possibility
Who is the service intended for?
- Local Internet providers
- Large and medium-sized companies
- Government and local government
Supplementary services
- ČDT-Telehousing – we provide the customer with space to place their own transmission technology in our data centers
- Primary and secondary DNS management
- Backup SMTP server for electronic mail
CDT-ANTIDDOS
Effective protection of customers against DDoS attacks.
The scrubbing centre's special deep traffic inspection technologies are able to determine which packets are regular customer traffic and which are components of a DDoS attack. The scrubbing centre intercepts DDoS attack packets and deflects them so that they are not passed on to the customer.
DDoS (Distributed Denial of Service) attacks are aimed at restricting the availability of a service (e.g. a website). A characteristic feature of an attack is that it mobilises a large number of IP addresses simultaneously (thus inhibiting simple blocking) and, at the same time, it is so strong that it can rapidly clog up the available transmission bandwidth, the system resources of the attack target and transport infrastructure components with ballast that is highly variable and impossible to foresee.
Effective protection against DDoS attacks requires the application of deep traffic inspection methods and mechanisms readily adaptable to various forms.
ČDT-ANTIDDOS is available as two different options:
- Scrubbing standby – when a DDoS attack is detected, traffic is rerouted to the scrubbing centre. Traffic is rerouted and scrubbing begins within 4 minutes of a launch of a DDoS attack.
- Continuous scrubbing – the subscriber's traffic is continuously routed via the scrubbing centre. Scrubbing begins within 1 minute of a DDoS attack.
Key benefits:
- Timely DDoS attack detection in internet connectivity
- Removal of ballast
- No service restrictions or unavailability
- Fully automatic solution with no need for manual intervention
- Much faster response time to a DDoS attack
- Less strain on the network operator's active components
The service intercepts the following types of attack:
- Attacks generated by known tools available on the internet
- DDoS traffic generated by known botnets
- SYN FLOOD
- TCP ACK + FIN FLOOD
- TCP RST FLOOD
- TCP SYN + ACK FLOOD
- TCP fragmentation FLOOD
- UDP FLOOD
- ICMP FLOOD
- IGMP FLOOD
Service target group:
- Local internet service providers
- Large and medium-sized companies
- Central and local government bodies
- Content providers
- News servers
- E-shop operators
- Financial institutions
ČDT-ANTIDDOS prevents:
- Service unavailability (customer's e-shop or website) triggered by a DDoS attack
- Losses caused by DDoS attacks that cannot be simply blocked by conventional means
- Congestion of available transmission bandwidth and system resources targeted by the attack
- Congestion of transport infrastructure components with ballast, which tends to be highly variable and impossible to foresee
- Unfair competitive practices via DDoS attacks
ČDT-ANTIDDOS is a supplementary service coupled with the internet access provided by ČD - Telematika.
CDT-Monitor
The CDT-MONITOR service enables customers to obtain an overview of security incidents on their Internet connectivity.
The CDT-MONITOR service allows the customer to keep track of security incidents on their Internet connectivity. By means of special probes the customer's Internet traffic is monitored, and the collected data is evaluated by methods detecting security risks.
With this product, the customer gets a quick summary of the security risks in their network (attacks against computers in the network, scanning computers, generating spam, etc.), enabling them to react quickly and minimise their impact on users.
Methods used
- Telnet – increased use of Telnet service. It detects all connections, including connection attempts on TCP port 23, and counts the number of these connections for individual IP addresses;
- SSHDICT – attempts to guess a username/password or login by means of a spurious certificate to the SSH service. The method is able to recognise a successful/unsuccessful attack;
- OUTSPAM – sending or attempting to send an increased number of e-mails from specific IP addresses;
- SCANS – various types and methods of scanning network. The details include the number of unique scans, a report on potential response of the scanned IP address, and a list of the ports involved. It indicates infected IP addresses in the network;
- DNSQUERY – an increased number of DNS queries from specific IP addresses;
- DNSANOMALY – suspicious communication in DNS traffic;
- BLACKLIST – traffic control (by assigned filters) and recognition of communication with the IP addresses included in the blacklist;
- RDP Dictionary Attacks – detects attempts to guess user names and passwords in RDP service. Dictionary attacks are a widespread and popular method to gain unauthorised access to a computer system.
- REFLECTDOS Amplificated DoS attack – detects DoS attacks that exploit certain service vulnerabilities to amplify themselves. They are able to generate a much larger response to a specific request that is then sent to the request's spoofed source IP address (e.g. via unsecured NTP servers).
Main benefits
- Early detection of risk traffic in the Internet connectivity
- Reduced burden on the active elements of the network operator
- Further development of wholesale partners' business activities towards end customers
Who is the service intended for?
- Local Internet providers
- Large and medium-sized companies
- Government and local government
The service is provided as a supplementary service to the Internet access provided by ČD - Telematika.
Report Example

Relevant Products and Services
ICT Services
Use our indepent datacentre for serverhousing
ICT Security
Information Security Services based on previous analysis